Blog page

Reverse engineering eBPF programs
Dive into the internals of how eBPF works by reverse engineering some eBPF-based programs
Read more
Unveiling Hidden Threats: Detecting Unauthorized Access in Kubernetes with eBPF
Dive deep into using eBPF for security, specifically detecting unauthorized access attempts
Read more
Aya Rust Tutorial part 5: Using Maps
Learn how to pass data between the kernel and user space using Maps in eBPF
Read more
Simple Firewall with Rust and Aya
Learn how to use eBPF to create a simple firewall/router
Read more
Zero to Performance Hero: How to Benchmark and Profile Your eBPF Code in Rust
Learn how to create a basic eBPF program in Rust
Read more
Transparent Proxy Implementation using eBPF and Go
Learn how to implement Transparent proxies with eBPF using the ebpf-go package
Read more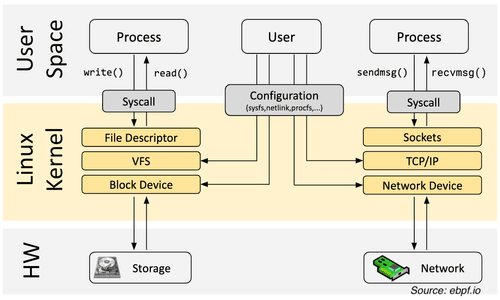
An Applied Introduction to eBPF with Go
Learn what eBPF is, how it works and how to use it with Go
Read more
Unleash the Forbidden - Enabling eBPF/XDP for Kernel Tinkering on WSL2
Learn how to run eBPF on WSl2 running on Windows 10
Read more
Intro to development using eBPF
Learn how to build a development docker container for eBPF and libbpf tooling
Read more
Hello eBPF: Global Variables (10)
The tenth installment of the Hello eBPF series. In this part, you'll learn how to use global variables to configure our eBPF and communicate between user-land and kernel-land
Read more