Blog page
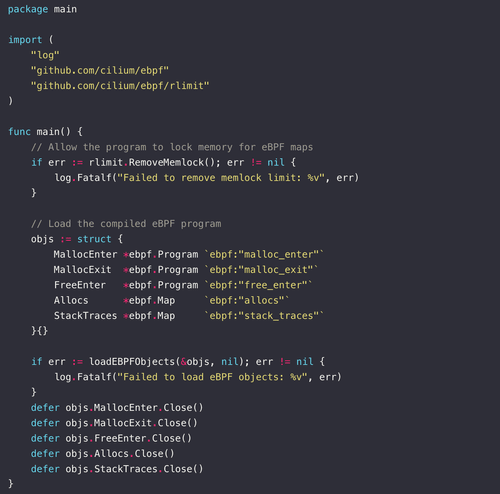
Debugging Memory Leaks with eBPF
Learn how eBPF and uprobes can be combined to trace memory allocations and detect leaks
Read more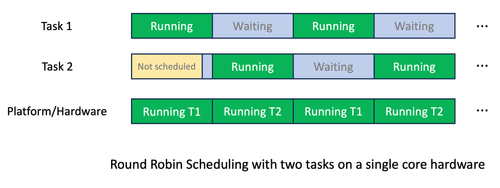
How to use eBPF for monitoring Linux thread contention?
Learn to create a minimal scheduler written with sched_ext in C
Read more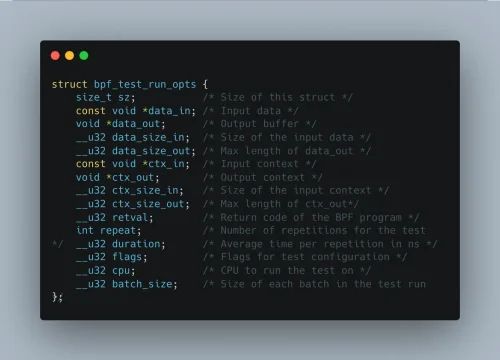
Unit Testing eBPF Programs
Learn how to test eBPF XDP programs
Read more
How to use eBPF for monitoring Linux thread contention?
Learn how to use eBPF for monitoring Linux thread contention
Read more
How to run code in kernel space? eBPF!
Learn about eBPF and how to write an eBPF program that capture network packets in the kernel with Go
Read more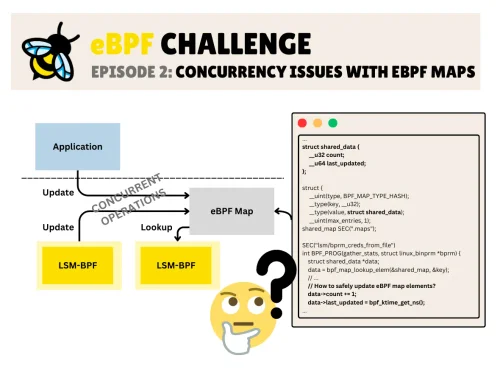
eBPF Challenge 3: eBPF Ring Buffer Optimizations
Learn how to optimize an eBPF Ring Buffer
Read more
eBPF Challenge 2: Concurrency Issues with eBPF Maps
An eBPF challenge that showcases how to ensure that your eBPF programs update the elements in a race-safe manner, ensuring no instance reads a partially updated structure?
Read more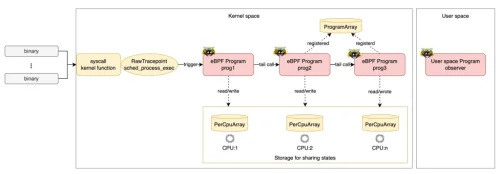
eBPF Tail Calls with Rust Aya
Learn how to implement eBPF Tail Calls using Rust’s Aya
Read more
How to write and run an eBPF program on Linux
A step-by-step guide to creating your first eBPF program and running it on a Linux system
Read moreeBPF Challenge 1: XDP Return Codes
An eBPF challenge that showcases the consequence of returning a 0 value from an XDP program
Read more