Blog page
Testing eBPF Program Compatibility Across Kernels with LVH and GitHub Actions
GitHub Actions Meets Little VM Helper and eBPF
Read more
Breaking Boundaries: Implementing the Enigma Machine in eBPF
André Martins celebrates Alan Turing 113th posthumous birthday by implementing the Enigma machine in eBPF
Read more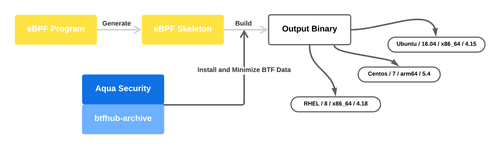
Why Does My eBPF Program Work on One Kernel but Fail on Another?
Learn how to make eBPF programs portable across different Linux kernels using BPF CO-RE and BTF, and discover techniques for supporting systems without built-in BTF by embedding external BTF data.
Read more
What If CI/CD Pipelines Had Built-in Security and Observability with eBPF?
Learn how eBPF can add real-time security and observability to CI/CD pipelines like GitHub Actions, helping detect exploits and optimize workflows execution time.
Read more
Case Study: Polar Signals Uses eBPF to Monitor Internal Cross-Zone Network Traffic on Kubernetes, Reducing These Operating Costs by 50%
Polar Signals developed kubezonnet, an open source project designed to monitor and measure cross-zone network traffic in Kubernetes clusters. The solution leverages eBPF to trace network packets and aggregate traffic data.
Read more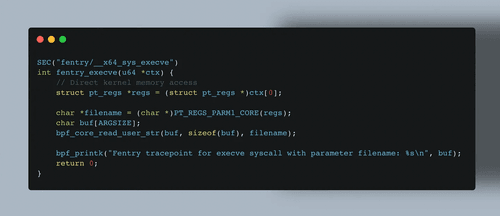
Tracepoints, Kprobes, or Fprobes: Which One Should You Choose?
Tracing programs like kprobes, fprobes, and tracepoints are very popular, but their overlapping functionality can make choosing the right one confusing.
Read more
P99Conf: How eBPF Could Make Faster Database Systems
Learn about BPF-DB, an in-memory key-value data store that can be planted within the OS kernel itself via eBPF, thereby routing around the restrictions and limitations of an OS’s user space, or the space in memory where a program is typically run
Read more
شروع برنامه نویسی در ebpf با یک مثال ساده
درباره eBPF و نحوه نوشتن برنامه eBPF بیاموزید
Read more
Transparent Packet Inspection with Netfilter and eBPF
Learn about transparent packet inspection with Netfilter and eBPF
Read more
Cloud Native Networking as Kubernetes Starts Its Second Decade
Dive into how Kubernetes networking and security circulatory systems will grow and adapt
Read more