Blog page
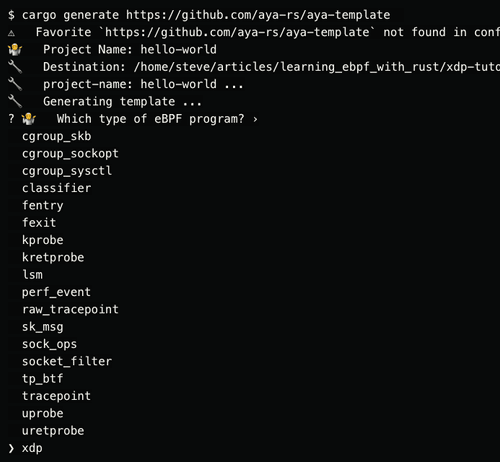
Aya Rust tutorial Part Four XDP Hello World
In the 4th part of the series, learn how to build an XDP program that prints a message every time it receives a packet on an interface
Read more
Transparent Proxy Implementation using eBPF and Go
Learn how to implement Transparent proxies with eBPF using the ebpf-go package
Read more
Modernizing BPF for the next 10 years
Explore the future development and modernization of BPF over the next decade, including proposed enhancements, and reflect on its evolution and current capabilities
Read more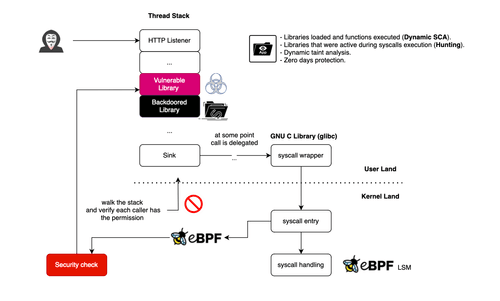
Profiling Libraries With eBPF: Detecting Zero-Day Exploits and Backdoors
Learn how to use eBPF for runtime application security to detect library profile deviations
Read more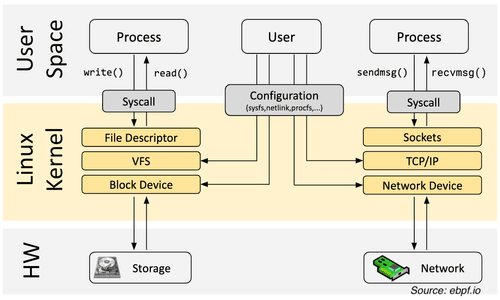
An Applied Introduction to eBPF with Go
Learn what eBPF is, how it works and how to use it with Go
Read more
Unleash the Forbidden - Enabling eBPF/XDP for Kernel Tinkering on WSL2
Learn how to run eBPF on WSl2 running on Windows 10
Read more
Wie eBPF die Logdaten-Sammlung revolutioniert
Erfahren Sie, wie eBPF die Protokoll- und Metrikerfassung revolutioniert hat
Read more
Intro to development using eBPF
Learn how to build a development docker container for eBPF and libbpf tooling
Read more
Hello eBPF: Global Variables (10)
The tenth installment of the Hello eBPF series. In this part, you'll learn how to use global variables to configure our eBPF and communicate between user-land and kernel-land
Read more
Demystifying eBPF with Liz Rice: A Deep Dive into Kernel Programming and Security
In this podcast, Liz sheds light on the evolution of eBPF from a packet filtering tool to a powerful kernel programming technology
Read more