Blog page

TechnologyExternal
The Silent Platform Revolution: How eBPF Is Fundamentally Transforming Cloud-Native Platforms
The next decade of infrastructure software will be defined by platform engineers who can use eBPF and the projects that leverage it to create the right abstractions for higher-level platforms.
Read more
TechnologyExternal
Unlocking the Power of Programmable Data Planes in Kubernetes with eBPF
Learn how eBPF is transforming modern cloud native environments
Read more
TechnologyExternal
eBPF Explained: Why it is Important for Observability
eBPF intro and uses for monitoring
Read more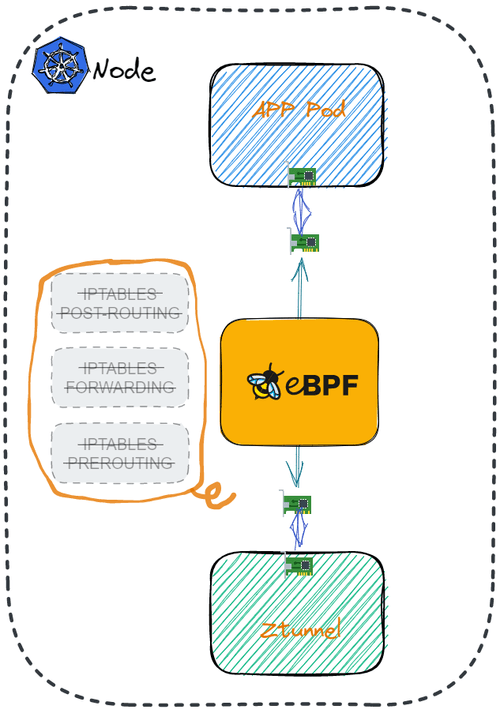
TechnologyExternal
Using eBPF for traffic redirection in Istio ambient mode
Another service mesh turns to eBPF
Read more
TechnologyExternal
One year of testing eBPF programs
What Exein learned in the past year
Read more
TechnologyExternal
eBPF for Cybersecurity - Part 3
Learn to use Rust and eBPF together
Read more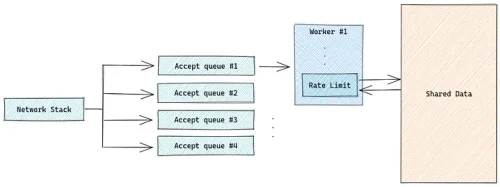
TechnologyExternal
We removed Shared-Memory by building an eBPF Load-Balancer
Find out how ArvanCloud utilized eBPF to create a high-performance load balancer for their network infrastructure
Read more
TechnologyExternal
How debugging Go programs with Delve and eBPF is faster
Learn how eBPF is faster than ptrace for tracing
Read more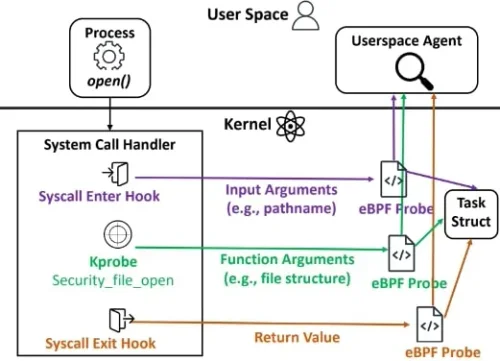
TechnologyExternal
CloudNativeSecurityCon 2023: Identifying Suspicious Behaviors with eBPF
The eBPF wrap up from CloudNativeSecurityCon
Read more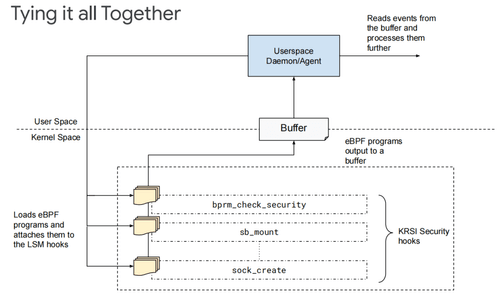
TechnologyExternal
What You Need to Know About eBPF Security Observability
Learn the advantages of using eBPF for Security Observability
Read more