Blog page
Kernel Introspection from Linux to Windows
Explore the transition from user-space monitoring to kernel-level introspection in cybersecurity, focusing on technologies like eBPF in Linux and similar advancements in Windows
Read more
Explorando eBPF: Uma Revolução na Observabilidade e Segurança de Sistemas
uma breve introdução ao eBPF
Read more
eBPF has opened many doors for Linux, will continue to do so for many years
ITOps Times reports on the recent release of the State of eBPF report by the Linux Foundation
Read more
eBPF for Linux Admins: Part VIII
The eighth piece of a series on getting started with eBPF for linux adminstrators
Read more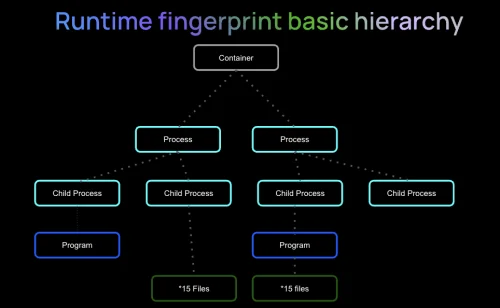
Verified runtime fingerprints to eliminate zero day software supply chain attacks
KSOC announce the availability of the eBPF-based RAD security standard, to help the cloud native security ecosystem combat the wave of software supply chain attacks
Read more
Introduction à l’eBPF
TUne plongée approfondie dans l'eBPF et les principaux concepts de la technologie
Read more
The state of eBPF - lwn.net
A thread of converations on lwn.net around the recently released State of eBPF report
Read more
Hello eBPF: Recording data in event buffers (3)
Learn how to use the perf_event_buffer eBPF map, and how to run tests with docker and JUnit
Read more
What is XDP after all?
A short guide on XDP highlighting its main audience, use cases and how to compile it
Read more
Diving into an eBPF + Go Example: Part 1
The first part of a three-parter on using eBPF and Go
Read more