Blog page

How to write and run an eBPF program on Linux
A step-by-step guide to creating your first eBPF program and running it on a Linux system
Read more
eBPF Is Coming for Windows
eBPF will soon offer cross-platform compatibility for in-kernel programs, for both Linux and Windows
Read more
Runtime Context: Missing Piece in Kubernetes Security
Learn about the crucial role of eBPF in enhancing Kubernetes security and how organization can levarge it to gain real-time insights, detect anomalies, and implement more effective security policies
Read more
The Past, Present, and Future of eBPF and Its Path to Revolutionizing Systems
Dive into eBPF's journey, explore where it’s headed in the next ten years, and learn about the challenges and opportunities that lie ahead
Read more
eBPF: Revolutionizing Observability for DevOps and SRE Teams
Learn why eBPF matters in modern observability
Read more
First eBPF program
Learn how to write a Python program that compiles and loads the eBPF program into the kernel and attaches it to the execve system call
Read more
How Cloudflare auto-mitigated world record 3.8 Tbps DDoS attack
Learn how Cloudflare were able to deal with a DDoS attack and protect their systems with XDP and eBPF
Read moreeBPF Challenge 1: XDP Return Codes
An eBPF challenge that showcases the consequence of returning a 0 value from an XDP program
Read more
eBPF- One Size Does Not Fit All
Explore how eBPF is not a "one size fits all" solution despite how it is becoming widely adopted for various use cases
Read more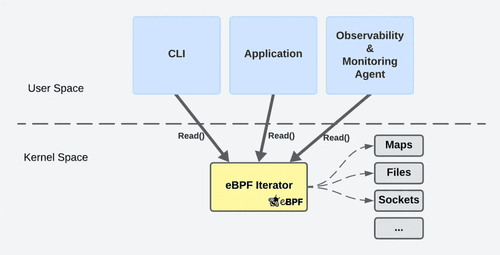
eBPF Map Monitoring using eBPF Iterators
eBPF Map Metrics Prometheus Exporter
Read more