Blog page

How Cloudflare auto-mitigated world record 3.8 Tbps DDoS attack
Learn how Cloudflare were able to deal with a DDoS attack and protect their systems with XDP and eBPF
Read moreeBPF Challenge 1: XDP Return Codes
An eBPF challenge that showcases the consequence of returning a 0 value from an XDP program
Read more
eBPF- One Size Does Not Fit All
Explore how eBPF is not a "one size fits all" solution despite how it is becoming widely adopted for various use cases
Read more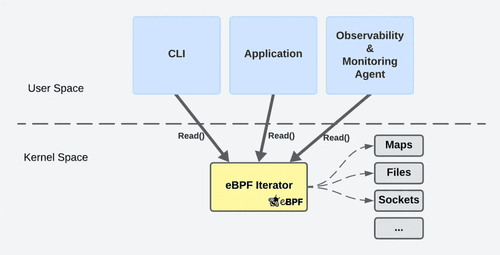
eBPF Map Monitoring using eBPF Iterators
eBPF Map Metrics Prometheus Exporter
Read more
Introduction to eBPF
Discover how eBPF allows developers to safely extend Linux kernel capabilities for observability, tracing, and security
Read more
CrowdStrike's Blue Screen blunder: Could eBPF have saved the day?
Grafana Labs CTO, Tom Wilkie, discusses eBPF and its role in preventing incidents such as the CrowdStrike Windows kernel crash, while also addressing cloud economics and open-source development
Read more
Tetragon eBPF for Kubernetes: The Verdict Is Out
Dive into Tetragon's effectiveness in improving security and observability for cloud-native applications running on Kubernetes
Read more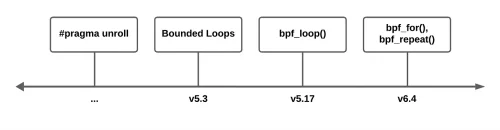
Loops and Iterators in eBPF
Learn how to use loops and iterators in eBPF and how to implement them effectively in eBPF applications
Read more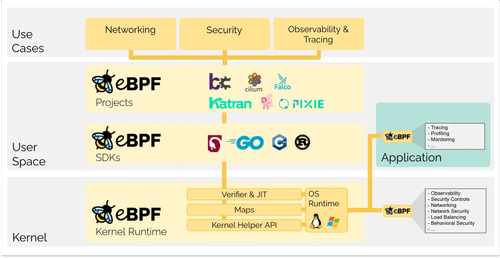
Observability With eBPF
Dive into eBPF, a technology that allows you to run sandboxed programs within the Linux kernel
Read more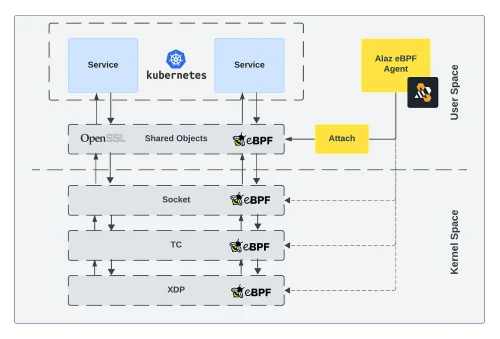
What Insights Can eBPF Provide into Real-Time SSL/TLS Encrypted Traffic and How?
Learn how eBPF user space probes (uprobes) can help bypass encryption limitations to monitor and interpret secure network traffic that traditional packet sniffers cannot
Read more