Blog page
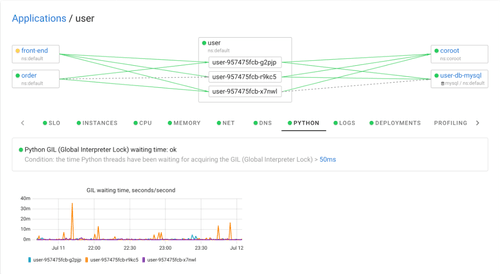
Instrumenting Python GIL with eBPF
Explore how to measure the impact of the Global Interpreter Lock (GIL) in Python using eBPF
Read more
eBPF map as communication channel
Dive into how eBPF maps can be repurposed for communication between userland applications and kernel drivers on Linux systems
Read more
Using eBPF to Deep Dive Into Functions in the Kernel
Learn about what eBPF is, how it works, and what its programming model is like
Read more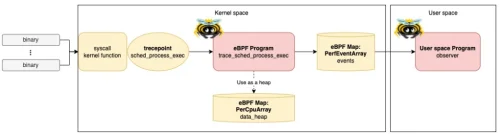
Writing eBPF Tracepoint Program with Rust Aya: Tips and Example
Learn how to write and run an eBPF Tracepoint program with Rust Aya
Read more
Talking eBPF and Cilium with Liz Rice
Liz Rice explains how eBPF works, what benefits and value it offers to enterprises looking to not only consolidate their observability of cloud native platforms and applications but also gain Linux kernel-level security and networking management
Read more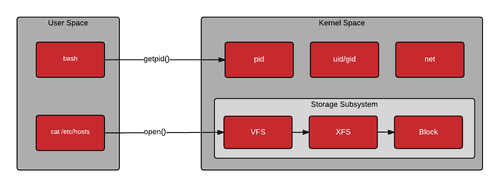
Go Weekly: Mastering Go Performance - eBPF and PGO Optimization Techniques
A list of posts on achieving PGO optimization with eBPF and an introduction to eBPF with Go
Read more
Aflevering 59: Unpacking eBPF and Sustainability
In deze aflevering legt Alessandro de complexiteit van eBPF-maps uit en hoe ze de beweging van data mogelijk maken
Read more
eBPF Network Vershitifier
Learn about eBPF Network Vershitifier, a simple ebpf-go application that randomly drops outgoing packets for targeted processes using the eBPF TC filters
Read more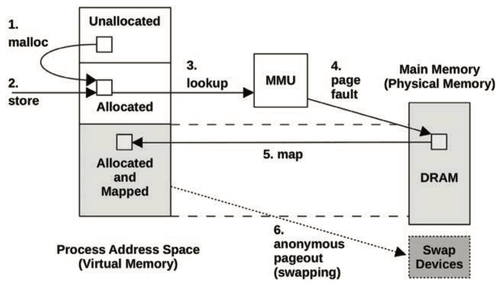
Memory Management on Kubernetes with Golang and eBPF: Deep Dive
An exploration on workload memory use, the memory control group, the OOM killer, and their relation with applications running on Kubernetes using Go and eBPF
Read more
The coming eBPF revolution and why Kubernetes monitoring will never be the same
Learn how eBPF revolutionizes Kubernetes monitoring by making the Linux kernel programmable, enhancing performance, visibility, and innovation. It also outlines the history of eBPF, its core use cases, and examples of major companies benefiting from its implementation
Read more