Blog page
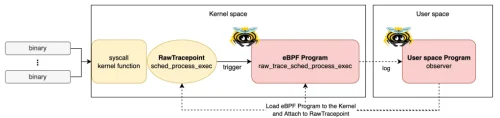
Writing eBPF RawTracepoint Program with Rust Aya
Learn how to write an eBPF RawTracepoint program using Aya with Rust
Read more
Challenges and Strategies in eBPF Uprobe Development
Learn where and how to discover and attach uprobes in the application stack
Read more
Re-implementing my Linux Rust scheduler in eBPF
Learn how a rust-based Linux scheduler was re-implemented with BPF
Read more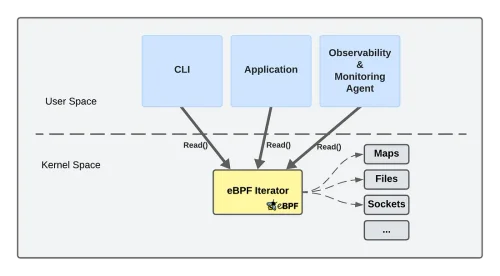
Part 2: eBPF Map Metrics Prometheus Exporter
Learn about eBPF Iterators and how to export eBPF Map metrics without altering your application stack
Read more
Introduction To Writing eBPF Programs for Linux Security
Learn about eBPF and how to write eBPF programs for Linux security
Read more
A deep dive into CVE-2023-2163: How we found and fixed an eBPF Linux Kernel Vulnerability
Learn about the discovery of CVE-2023-2163, a vulnerability within the eBPF verifier, what the root-cause analysis process looked like, and what was done to fix the issue
Read more
extended Berkeley Packet Filter (eBPF) for Cloud Computing
Learn about eBPF and how it is used today in cloud computing
Read more
Go deeper: Linux runtime visibility meets Wireshark
Aqua announces Traceeshark, a plugin for Wireshark that enables visual and interactive analysis of eBPF-based Tracee events, which include kernel-level events and behavioral detections, together with network traffic
Read more
Upwind Extends its CNAPP with Agentless Cloud Scanners
Upwind announces Upwind Agentless Cloud Scanners, an additional component to their eBPF-based sensor which provides unified, comprehensive coverage for infrastructure and applications, across clouds, platforms and architectures
Read more
eBPF Insights Into Real-Time SSL/TLS Monitoring
Learn about how eBPF can help intercept and monitor SSL/TLS encrypted traffic
Read more