Blog page
TechnologyExternal
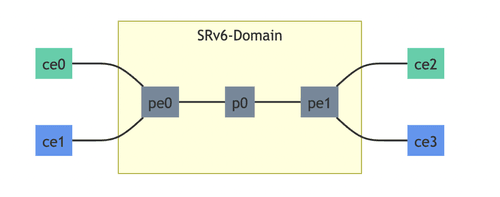
Zebra BPF DPlane Demo
FRRouting meets eBPF
Read more
CommunityExternal
「eBPF」がクラウドネイティブを超強力にする。eBPFとは何か? 何ができて、どんな利点があるのか? Cloud Native Days Tokyo 2022基調講演から
「eBPF」がクラウドネイティブを超強力にする。eBPFとは何か? 何ができて、どんな利点があるのか? Cloud Native Days Tokyo 2022基調講演から
Read more
CommunityExternal
Meet Groundcover - The Startup That’s Building The Next-Gen Observability Stack
Learn about how Groundcover is leveraging eBPF from Forbes
Read more
CommunityExternal
groundcover 2023 Predictions: The Rise of eBPF
The rise of eBPF frictionless instrumentation will cause a major shift in the industry towards solutions that offer immediate time-to-value
Read more
CommunityExternal
Why a DevOps/SRE or Network Engineer should know about eBPF and how it is going to make a revolution?
A very brief introduction
Read moreTechnologyExternal
Finally making use of bpftrace
A simple example to get started with bpftrace
Read more
TechnologyExternal
从编译到可执行,eBPF 加速容器网络原理分析
从编译到可执行,eBPF 加速容器网络原理分析
Read more
TechnologyExternal
eBPF - A new frontier for malware
Learn how eBPF is being used in malware and how to mitigate it
Read more
TechnologyExternal
Using eBPF and predefined inspections to minimize observability tax
Learn how to make observability easy with eBPF
Read moreTechnologyExternal
Kafka Monitoring with eBPF: It’s a Whole New Perspective
Learning why Kafak monitoring needs eBPF
Read more