Blog page
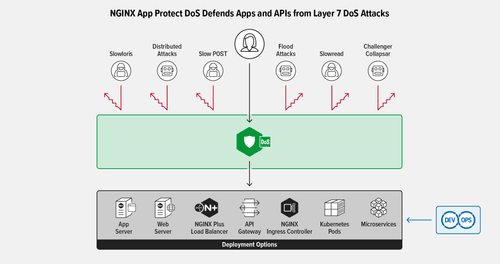
Accelerating DDoS Mitigation with eBPF in F5 NGINX App Protect DoS
Learn how NGINX is leveraging eBPF
Read more
eBPF Explained: Why it is Important for Observability
eBPF intro and uses for monitoring
Read more
Announcing eBPF 2.0: excelBPF™
Hear about the latest innovation from the eBPF community, turn your cells into hives of activity
Read more
Demystifying eBPF Tracing: A Beginner's Guide to Performance Optimization
Dive into how eBPF tracing works
Read more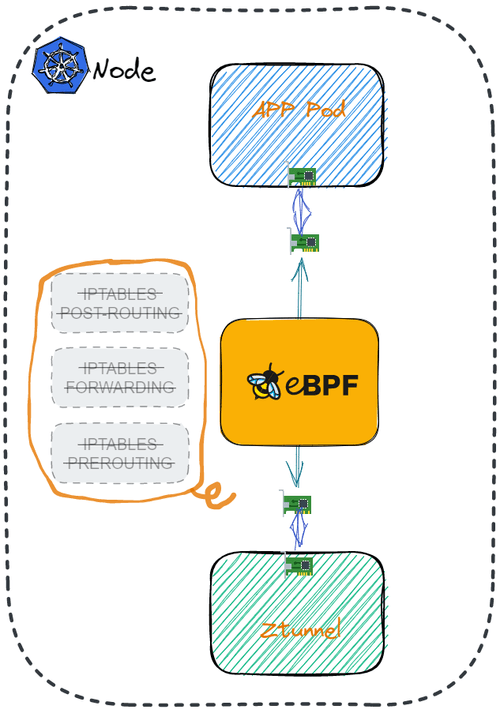
Using eBPF for traffic redirection in Istio ambient mode
Another service mesh turns to eBPF
Read more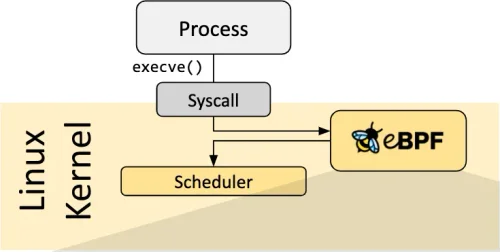
eBPF: The Emerging Linux Kernel Technology Explained
A quick introduction
Read more
Rethinking the Linux kernel with eBPF
History and intro to eBPF
Read more
Accelerate network packets transmission with eBPF
This article explores using eBPF to reduce latency by enabling direct data transmission between two sockets in the same kernel space, bypassing the kernel protocol stack for quicker packet delivery
Read more
eBPF programming on Windows
We’ll be looking at setting up a Windows-eBPF build environment, followed by creating a sample project to pass around data between a userspace program and an eBPF program running in the kernel.
Read more
How eBPF unlocks cloud native innovation
By allowing Linux kernel capabilities to be extended without changing kernel source code, eBPF is bringing faster innovation, more efficient networking, and greater performance and scalability to the cloud native stack
Read more