Blog page

Want to Stop Kernel Panics? Use eBPF
Learn how how eBPF can be used to prevent kernel panics by allowing developers to write kernel-level code that is safer and more controlled
Read more
How the CrowdStrike Tech Outage Reignited a Battle Over the Heart of Microsoft Systems
Learn how eBPF might have prevented the recent CrowdStrike outage in Windows systems
Read more
eBPF for Security
Learn how organizations are using eBPF for security, as a new ubiquitous technology to protect their workloads
Read more
Hello eBPF: A Packet Logger in Pure Java using TC and XDP Hooks (13)
The thirteenth installment of the Hello eBPF series. In this part, you’ll learn how to build a packet logger in pure Java using TC and XDP hooks
Read more
eBPF TLS tracing: The Past, Present and Future
Explore the TLS tracing tactics used by open source projects, how they've evolved to address these unstable user space library interfaces and where the future is headed
Read more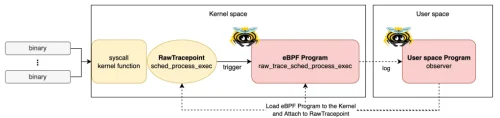
Writing eBPF RawTracepoint Program with Rust Aya
Learn how to write an eBPF RawTracepoint program using Aya with Rust
Read more
Challenges and Strategies in eBPF Uprobe Development
Learn where and how to discover and attach uprobes in the application stack
Read more
Re-implementing my Linux Rust scheduler in eBPF
Learn how a rust-based Linux scheduler was re-implemented with BPF
Read more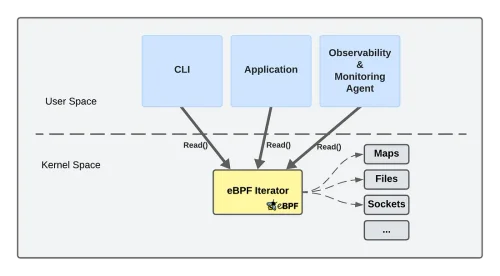
Part 2: eBPF Map Metrics Prometheus Exporter
Learn about eBPF Iterators and how to export eBPF Map metrics without altering your application stack
Read more
A deep dive into CVE-2023-2163: How we found and fixed an eBPF Linux Kernel Vulnerability
Learn about the discovery of CVE-2023-2163, a vulnerability within the eBPF verifier, what the root-cause analysis process looked like, and what was done to fix the issue
Read more