Blog page
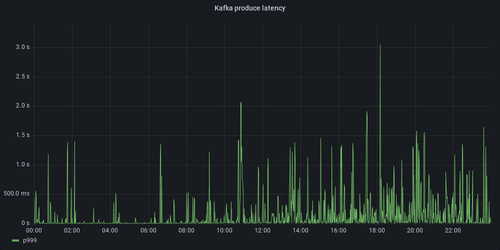
Unlocking Kafka's Potential: Tackling Tail Latency with eBPF
Learn how Allegro used Kafka protocol sniffing and eBPF to identify and remove root cause of slow produce requests in their Kafka cluster
Read more
eBPF, mit und ohne Cilium
In diesem Beitrag geht es um Cilium, eBPF und die Übernahme von Isovalent durch Cisco
Read more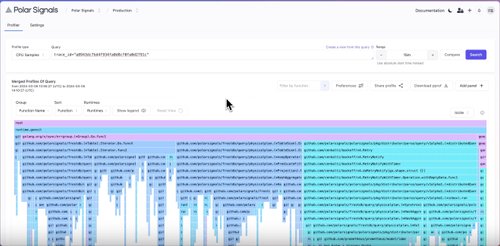
Correlating Tracing with Profiling using eBPF
Learn how to use ebpf-based Parca-Agent to read the trace ID from a target program with Go
Read more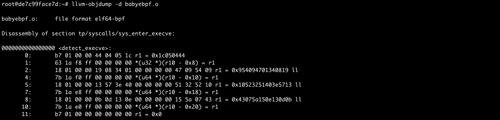
An Introduction to Reverse Engineering for eBPF Bytecode
Learn how an eBPF program is structured and processed by reverse engineering it
Read more
How AI/ML combines with eBPF to help troubleshoot, secure, monitor Linux networking
A comprehensive guide on what eBPF is and predictions on how it may evolve
Read more
Netflix Releases bpftop: An eBPF-Based Application Monitor
TheNewStack reports on Netflix new eBPF-based application monitoring tool known as bpftop
Read more
Announcing bpftop: Streamlining eBPF performance optimization
Netflix announce bpftop, a command-line tool designed to streamline the performance optimization and monitoring of eBPF programs
Read more
Hello eBPF: First steps with libbpf (5)
The Fifth installment of the Hello eBPF series. In this part, you'll learn why you should use libbpf over libbcc
Read more
How eBPF has changed the way I feel about observability
Explore the disruptive potential of eBPF in the observability landscape and learn about groundcover's approach to utilizing eBPF for more efficient, flexible, and cost-effective observability solutions in cloud environments
Read more
Snooping on libpam (openssh auth, passwd) with Golang and eBPF
A detailed exploration of using eBPF and Golang to monitor and capture authentication credentials handled by libpam, specifically focusing on snooping on libpam as used by OpenSSH
Read more