Blog page

Cilium, eBPF and Beyond
Liz Rice discusses her involvement with several open source projects such as the Cilium project and eBPF
Read more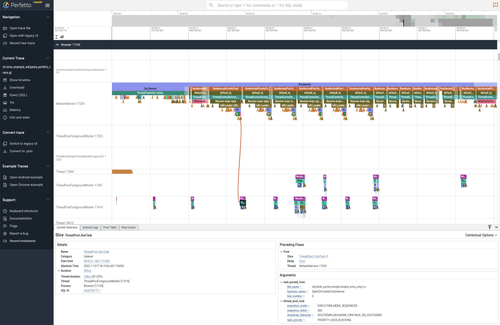
All my favorite tracing tools: eBPF, QEMU, Perfetto, new ones I built and more
A comprehensive guide to various tracing methods used to understand and diagnose issues in program execution
Read more
Signaling from within: how eBPF interacts with signals
A comprehensive examination of the complexities and technicalities of eBPF's interaction with UNIX signals, shedding light on both its potential and its challenges in the context of security and system resource management
Read more
The Secure Path Forward for eBPF runtime: Challenges and Innovations
Delve into eBPF security, learn about the role of the eBPF verifier and explore how the mechanisms intended to safeguard eBPF can themselves be fortified
Read more
EBPF-Based Security Solutions: Exploring Weaknesses And Mitigation Techniques
Learn about eBPF key vulnerabilities and mitigations to keep your systems secure
Read more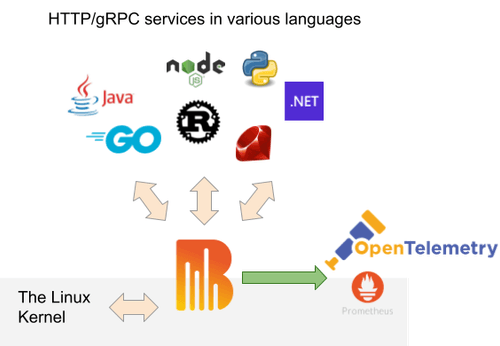
Grafana Beyla 1.0 release: zero-code instrumentation for application telemetry using eBPF
Grafana announce the release of Beyla 1.0, an open source eBPF auto-instrumentation tool. Learn about the basics and major features of Grafana Beyla
Read more
CoreTechnologys - How to drop 1 Tbps of DDoS traffic
Discover how CoreTechnologys tackled a DDoS attack using eBPF/XDP-powered hardware to efficiently filter out malicious traffic at their network's edge
Read more
KubeCon points to the future of enterprise IT
Explore the strategic shifts in enterprise IT at KubeCon, highlighting the significance of open-source projects like eBPF/Cilium and Tetragon in shaping cloud infrastructure and enhancing security in distributed computing
Read more
How to Use eBPF Capabilities to Navigate Kubernetes Monitoring
Learn how eBPF can be used to elevate your Kubernetes monitoring strategy by setting up an eBPF environment to monitor Kubernetes
Read more
The Big Interview: Thomas Graf, CTO, Isovalent, on eBPF, cloud-native networking and why Cilium is so hot right now
The Stack features Thomas Graf, CTO of Isovalent, discussing Cilium, an ebpf-based project for cloud native networking. Thomas highlighted Cilium's impact on cloud native networking, noting its rapid ascent as an eBPF-based standard for secure Kubernetes networking
Read more