Blog page

Leveraging eBPF for Improved Infrastructure Observability
A summary of Netflix's publication on using eBPF for detecting noisy neighbor
Read more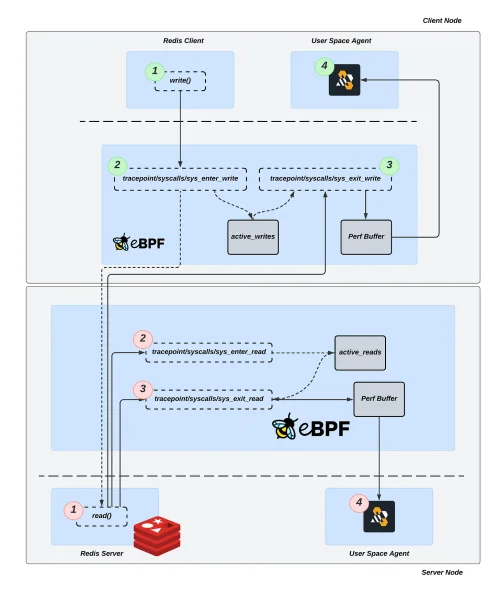
Can eBPF Detect Redis Message Patterns Before They Become Problems?
Learn how eBPF can efficiently monitor Redis deployments to identify and troubleshoot performance issues
Read more
What is the whole buzz around eBPF?
Learn what is eBPF and how it works
Read more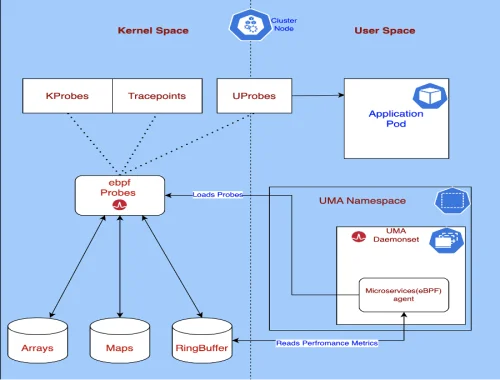
Introducing The eBPF Agent: A New, No-Code Approach for Cloud-Native Observability
Broadcom announce a new eBPF monitoring agent that provides comprehensive insights into the performance and interactions of frontends, backends, and application flows
Read more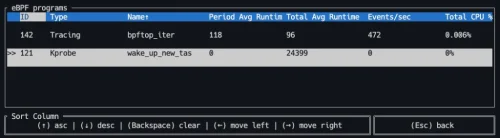
Writing eBPF Kprobe Program with Rust Aya
Learn how to write an eBPF Kprobe program using Aya with Rust
Read more
eBPF Summit 2024 Provides a Data-Driven Revolution
Learn about the basics of eBPF and get a review of the recently concluded eBPF summit 2024
Read more
Hacking eBPF & LLVM for Fun and Profit
Explore how eBPF and LLVM can be used for practical hacking, focusing on low-level code manipulation for performance and observability enhancements
Read more
Hello eBPF: Collection of Resources for eBPF (14.5)
The second part of the fourteenth installment of the Hello eBPF series. In this part, you'll find resources to help you get started with eBPF
Read more
Noisy Neighbor Detection with eBPF
Learn how Netflix leveraged eBPF to achieve continuous, low-overhead instrumentation of the Linux scheduler, enabling effective self-serve monitoring of noisy neighbor issues
Read more
eBPF Load Balancer
Learn how to build a load balancer with eBPF
Read more