Blog page

How-ToExternal
Writing an eBPF Application
Write a native eBPF application using libbpf
Read more
TechnologyExternal
One year of testing eBPF programs
What Exein learned in the past year
Read more
TechnologyExternal
eBPF for Cybersecurity - Part 3
Learn to use Rust and eBPF together
Read more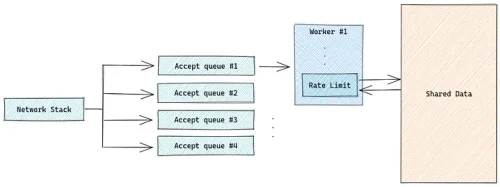
TechnologyExternal
We removed Shared-Memory by building an eBPF Load-Balancer
Find out how ArvanCloud utilized eBPF to create a high-performance load balancer for their network infrastructure
Read more
CommunityExternal
What is eBPF?
A quick introduction to eBPF
Read more
TechnologyExternal
How debugging Go programs with Delve and eBPF is faster
Learn how eBPF is faster than ptrace for tracing
Read more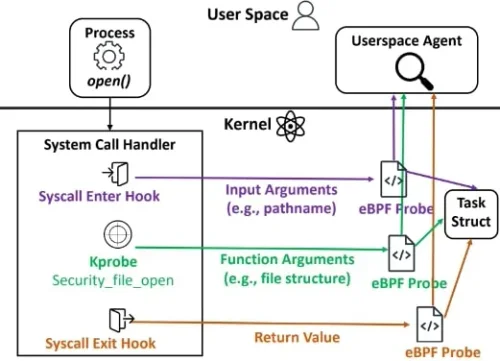
TechnologyExternal
CloudNativeSecurityCon 2023: Identifying Suspicious Behaviors with eBPF
The eBPF wrap up from CloudNativeSecurityCon
Read more
CommunityExternal
How AWS uses eBPF to identify security risks
Get an introduction to GuardDuty
Read more
How-ToExternal
eBPF for Cybersecurity - Part 2
Learn how to create an eBPF program
Read more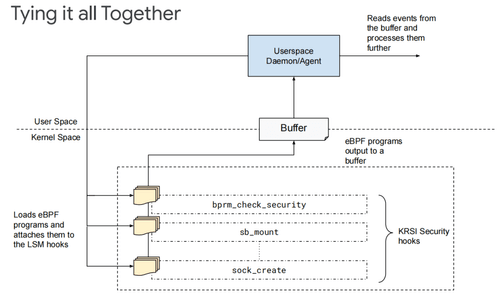
TechnologyExternal
What You Need to Know About eBPF Security Observability
Learn the advantages of using eBPF for Security Observability
Read more