Blog page
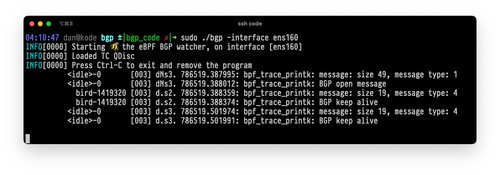
Perfecting Protocol Parsing (Probably) with eBPF
Learn how to parse BGP messages with eBPF
Read more
Unlocking the Power of eBPF at Traceable
Learn how Tracebale use eBPF for enhanced data collection
Read more
XDP and eBPF for Network Observability with Python
Explore observability with eBPF and Python by extending a packet counter example from Liz's Learning eBPF book
Read more
eBPF for Linux Admins: Part IV
The fourth piece of a series on getting started with eBPF for linux adminstrators
Read more
Hello eBPF: Recording data in basic eBPF maps (2)
In the second post in the series, hello-ebpf gained support for basic eBPF hash maps and the ability to store structures in these maps
Read more
Emre Sevinç's Review of Learning eBPF
A short positive review of Liz Rice's Learning eBPF book
Read more
Unveiling eBPF Verifier Errors - Episode 1
Learn what eBPF Verifier is, why it's necessary, how to address limitations imposed by the verifier
Read more
Networking and eBPF Predictions for 2024 and Beyond
Nico Vibert from Isovalent compiled his predictions for eBPF and Networking in 2024
Read more
Cisco Acquires Isovalent, Creator of eBPF: Why It Matters
An overview of eBPF, how ThreatX uses eBPF and why Cisco's acquisition of Isovalent matters
Read more
eBPF - Unleash the Linux kernel
An Overview of what eBPF entails and eBPF-based tools for tracing, security and observability
Read more