Blog page

Aflevering 59: Unpacking eBPF and Sustainability
In deze aflevering legt Alessandro de complexiteit van eBPF-maps uit en hoe ze de beweging van data mogelijk maken
Read more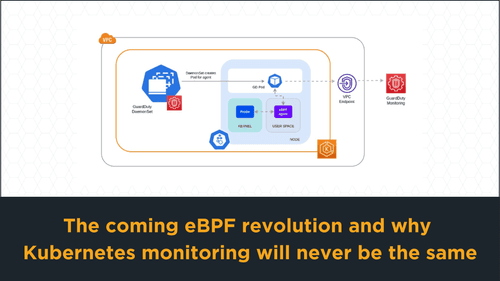
The coming eBPF revolution and why Kubernetes monitoring will never be the same
Learn how eBPF revolutionizes Kubernetes monitoring by making the Linux kernel programmable, enhancing performance, visibility, and innovation. It also outlines the history of eBPF, its core use cases, and examples of major companies benefiting from its implementation
Read more
Hello eBPF: BPF Type Format and 13 Thousand Generated Java Classes (11)
The eleventh installment of the Hello eBPF series. In this part, you’ll learn about the BPF Type Format (BTF) and how and why we generate Java code from it
Read more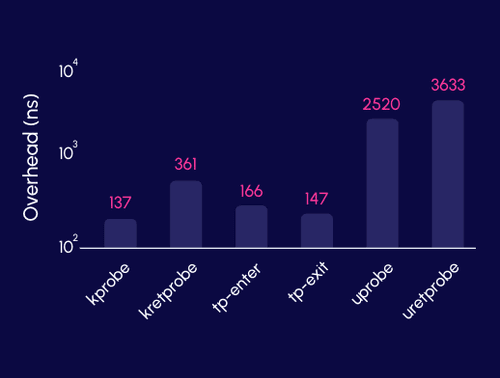
App-Level eBPF Applications - User vs. Kernel Probes
Learn about the two most popular methods for implementing eBPF instrumentation to gain application context in the runtime, by using user-space and kernel probes - and understand how each impacts the application performance and compute cost
Read more
Fooling Port Scanners: Simulating Open Ports with eBPF and Rust
Learn how to use Rust and eBPF to thwart curious individuals attempting to scan a machine using the three-way handshake behavior and a related port scanning technique
Read more
Monitoring PostgreSQL Database on Kubernetes using eBPF
Learn how to use eBPF for monitoring PostgreSQL databases on Kubernetes
Read more
Reverse engineering eBPF programs
Dive into the internals of how eBPF works by reverse engineering some eBPF-based programs
Read more
How eBPF is shaping the future of Linux and platform engineering
Explore eBPF's origins, its impact on modernizing the kernel for cloud native use cases, and how it is becoming mainstream through projects like Cilium, Tetragon, and Pixie
Read more
Unveiling Hidden Threats: Detecting Unauthorized Access in Kubernetes with eBPF
Dive deep into using eBPF for security, specifically detecting unauthorized access attempts
Read more
The Use of eBPF in Observability Today
Explore some of the specific technical and functional aspects of the use of eBPF in a number of leading obserability products
Read more