Blog page

The Use of eBPF in Observability Today
Explore some of the specific technical and functional aspects of the use of eBPF in a number of leading obserability products
Read more
Securing Linux Systems with eBPF: The Future of In-Kernel Observability and Security
Learn about eBPF, its integration with Linux, applications in monitoring and securing systems, and more
Read more
eBPF 如何重塑可观察性工程(第一部分
了解领先的可观察性平台如何在其工具中利用 eBPF 的强大功能
Read more
eBPF: Enabling security and performance to co-exist
Explore how eBPF enhances Linux kernel customization, enabling improved security and performance while offering deeper visibility and efficient packet processing in cloud native environments
Read more
A simple pair of eBPF tracepoint handlers
Learn about tracepoint handlers in eBPF
Read more
eBPF Cheat Sheet
A compilation of useful eBPF commands for a DevSecOps workflow
Read more
Aya Rust tutorial Part Four XDP Hello World
In the 4th part of the series, learn how to build an XDP program that prints a message every time it receives a packet on an interface
Read more
Modernizing BPF for the next 10 years
Explore the future development and modernization of BPF over the next decade, including proposed enhancements, and reflect on its evolution and current capabilities
Read more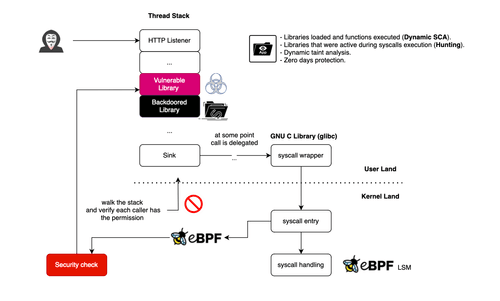
Profiling Libraries With eBPF: Detecting Zero-Day Exploits and Backdoors
Learn how to use eBPF for runtime application security to detect library profile deviations
Read more
Wie eBPF die Logdaten-Sammlung revolutioniert
Erfahren Sie, wie eBPF die Protokoll- und Metrikerfassung revolutioniert hat
Read more