Blog page

Hello eBPF: First steps with libbpf (5)
The Fifth installment of the Hello eBPF series. In this part, you'll learn why you should use libbpf over libbcc
Read more
How eBPF has changed the way I feel about observability
Explore the disruptive potential of eBPF in the observability landscape and learn about groundcover's approach to utilizing eBPF for more efficient, flexible, and cost-effective observability solutions in cloud environments
Read more
Snooping on libpam (openssh auth, passwd) with Golang and eBPF
A detailed exploration of using eBPF and Golang to monitor and capture authentication credentials handled by libpam, specifically focusing on snooping on libpam as used by OpenSSH
Read more
Get Started with eBPF Network Log Analytics in your Kubernetes Cluster
Learn how to audit external connections from a Kubernetes cluster and get valuable insights to protect your cluster with Parseable, eBPF and Tetragon
Read more
How eBPF has changed the way I feel about observability
In this interview, Bill Mulligan from the eBPF Foundation dives into the State of eBPF Report which details eBPF adoption within Linux that is fundamentally changing the way IT is managed
Read more
How eBPF Benefits IT Operations Teams Seeking to Improve Observability
A guide on why ITOps teams should consider taking advantage of eBPF, and how they can do so
Read more
Java and eBPF--airhacks.fm podcast
The #281 airhacks.fm episode with Johannes Bechberger about developing eBPF programs with Java and migrating Python tooling to Java with Project Panama
Read more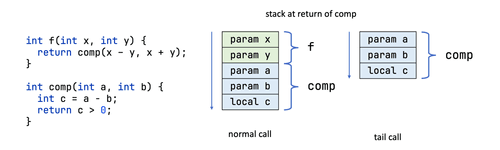
Hello eBPF: Tail calls and your first eBPF application (4)
In the 4th part of the series, you'll finish the chapter 2 of the Learning eBPF book, learn how to use tail calls and the hello-ebpf project as a library and implement one of the book’s exercises
Read more
Cisco's eBPF Gambit: A Game Changer in Cloud Native Security?
A short report on Cisco's acquisition of Isovalent highligting the benefits Cisco can get out of the deal and how they can leverage eBPF
Read more
Adventures in eBPF
An exploration of eBPF highlighting how build a program that leverages eBPF to intercept SSL traffic in user-space
Read more