Blog page

Exploring eBPF: A New Approach to Observing Kubernetes Workloads
Explore how Cisco uses eBPF technology for enhancing Kubernetes observability within Cisco Cloud Observability, and its application to solving customer challenges
Read more
eBPF Tracepoints: Gaining Access to the TCP State Machine
Learn how to create an eBPF program with kernel-land and user-land components to display every TCP connections state whenever the state machine is triggered
Read more
Using eBPF and XDP to Share Default DNS Port Between Multiple Resolvers
Learn how the NetBird team overcame the challenges of configuring DNS on Linux with eBPF and XDP to simplify DNS management in private WireGuard networks
Read more
Kernel Introspection from Linux to Windows
Explore the transition from user-space monitoring to kernel-level introspection in cybersecurity, focusing on technologies like eBPF in Linux and similar advancements in Windows
Read more
eBPF: Revolutionizing Observability for DevOps and SRE Teams
Learn how eBPF enhances observability for DevOps and SRE teams, and discover how Stackstate leverages eBPF for advanced observability
Read more
Explorando eBPF: Uma Revolução na Observabilidade e Segurança de Sistemas
uma breve introdução ao eBPF
Read more
eBPF has opened many doors for Linux, will continue to do so for many years
ITOps Times reports on the recent release of the State of eBPF report by the Linux Foundation
Read more
eBPF for Linux Admins: Part VIII
The eighth piece of a series on getting started with eBPF for linux adminstrators
Read more
Introduction à l’eBPF
TUne plongée approfondie dans l'eBPF et les principaux concepts de la technologie
Read more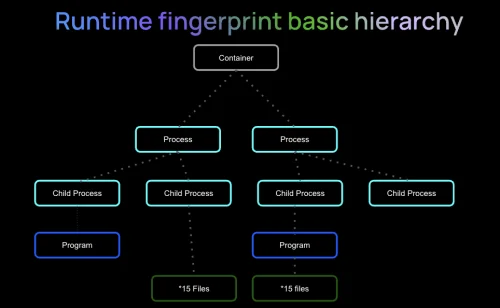
Verified runtime fingerprints to eliminate zero day software supply chain attacks
RAD Security announces the availability of the eBPF-based RAD security standard, to help the cloud native security ecosystem combat the wave of software supply chain attacks
Read more