Blog page

Seccomp, eBPF, and the Importance of Kernel System Call Filtering
Learn about attacks that affect user space security products and how popular technologies such as Seccomp and eBPF can be used in such a way that avoids these issues
Read more
How is Kubernetes Network Security Evolving?
In this podcast, Liz Rice spoke on Cilium, Tetragon and eBPF's impact in network security
Read more
eBPF’s User Ring Buffer: Introducing BPF_MAP_TYPE_USER_RINGBUF
Learn about BPF map types and the User Ring Buffer map type
Read more
How to Manage XDP/eBPF Effectively for Better DDoS Protection
Learn all about the techniques Gcore uses in their DDoS Protection product to effectively use xDP/eBPF
Read more
eBPF: Reliable Policy Setting and Enforcement
An exploration on the capabilities of eBPF in setting and enforcing reliable policies across various layers of the software stack. This piece discusses how eBPF enhances security, monitoring, and also argues that eBPF's utility extends beyond just Linux environments, highlighting its adaptability and impact on a broader range of operating systems
Read more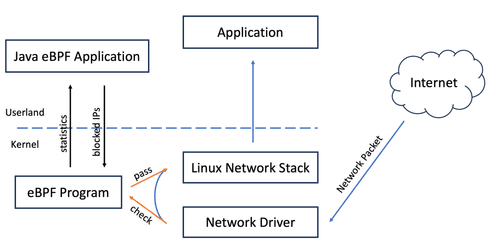
Hello eBPF: XDP-based Packet Filter (9)
The ninth installment of the Hello eBPF series. In this part, you'll learn how to use XDP and eBPF to create a partial packet filter that is easily extended into a firewall and blocks incoming packets
Read more
Elastic Universal Profiling agent, a continuous profiling solution, is now open source
Elastic announce that their ebpf-based Elastic Universal Profiling™ agent is now open source
Read more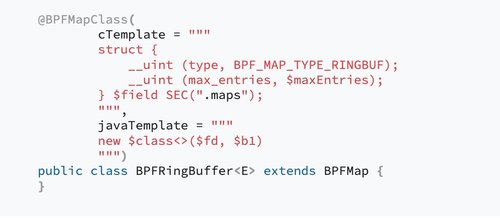
Hello eBPF: Generating C Code (8)
The eight installment of the Hello eBPF series. In this part, you'll learn how to use eBPF annotation processing to reduce the amount of C code needed and reduces errors
Read more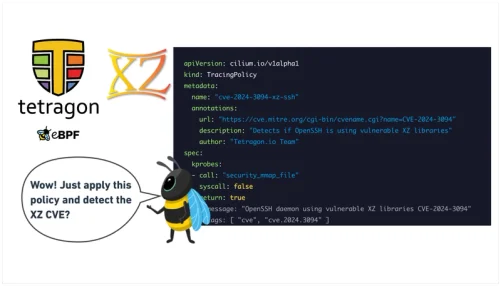
eBPF & Tetragon: Tools for detecting XZ Utils CVE 2024-3094 Exploit
Learn how to use Tetragon, an eBPF-based runtime security tool to detect the XZ backdoor in OpenSSH
Read more
#023 - Kubernetes for Humans Podcast with Liz Rice (Isovalent)
Liz Rice jumps on the Kubernetes for Humans podcast to talk about the use cases and future of eBPF
Read more