Blog page

Seccomp, eBPF, and the Importance of Kernel System Call Filtering
Learn about attacks that affect user space security products and how popular technologies such as Seccomp and eBPF can be used in such a way that avoids these issues
Read more
eBPF’s User Ring Buffer: Introducing BPF_MAP_TYPE_USER_RINGBUF
Learn about BPF map types and the User Ring Buffer map type
Read more
eBPF: Reliable Policy Setting and Enforcement
An exploration on the capabilities of eBPF in setting and enforcing reliable policies across various layers of the software stack. This piece discusses how eBPF enhances security, monitoring, and also argues that eBPF's utility extends beyond just Linux environments, highlighting its adaptability and impact on a broader range of operating systems
Read more
#023 - Kubernetes for Humans Podcast with Liz Rice (Isovalent)
Liz Rice jumps on the Kubernetes for Humans podcast to talk about the use cases and future of eBPF
Read more
Exploring eBPF Implementation through Linux Source Code
Dive into how eBPF works in the kernel by exploring the Linux source code
Read more
New State of eBPF Report highlights evolution of eBPF technology
Bill Mulligan, marketing committee at the eBPF Foundation talks about the recently released state of eBPF report and some of the emerging trends coming out of the eBPF ecosystem
Read more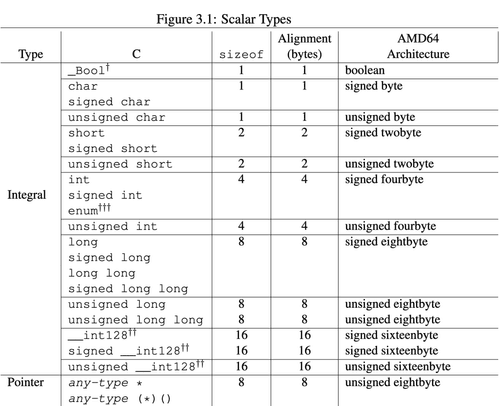
Hello eBPF: Auto Layouting Structs (7)
The seventh installment of the Hello eBPF series. In this part, you'll learn about the memory layout and alignment of structs transferred between the kernel and user-land in eBPF
Read more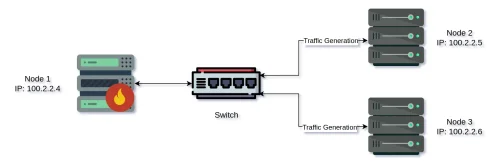
iptables vs. GoXDP: The Ultimate Packet Filtering Benchmark Setup and Results
Learn about the benchmark environment setup and the results of the Linux firewall tools (iptables and GoXDP). Discover the maximum number of packets that can be dropped per second when CPU utilization reaches 100%
Read more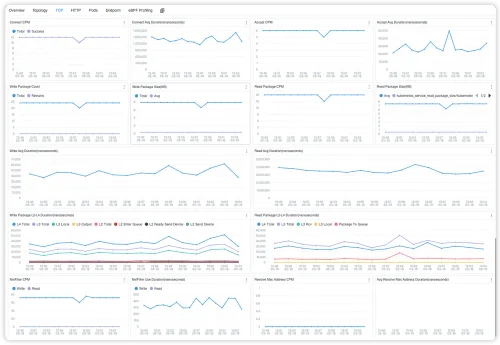
Monitoring Kubernetes network traffic by using eBPF
Learn how how SkyWalking uses eBPF to monitor network traffic on Kubernetes
Read more
How NeuVector Leverages eBPF to Improve Observability and Security
Learn how Neuvector, a cloud native security solution, uses eBPF for enhanced observability and security
Read more