Blog page

How to Manage XDP/eBPF Effectively for Better DDoS Protection
Learn all about the techniques Gcore uses in their DDoS Protection product to effectively use xDP/eBPF
Read more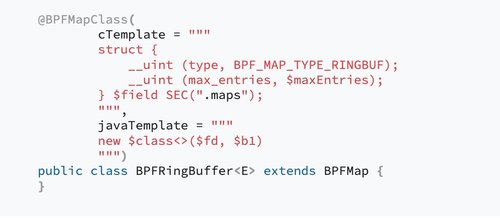
Hello eBPF: Generating C Code (8)
The eight installment of the Hello eBPF series. In this part, you'll learn how to use eBPF annotation processing to reduce the amount of C code needed and reduces errors
Read more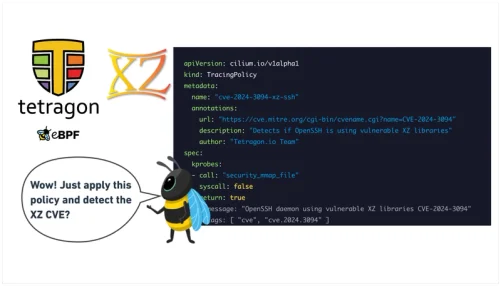
eBPF & Tetragon: Tools for detecting XZ Utils CVE 2024-3094 Exploit
Learn how to use Tetragon, an eBPF-based runtime security tool to detect the XZ backdoor in OpenSSH
Read more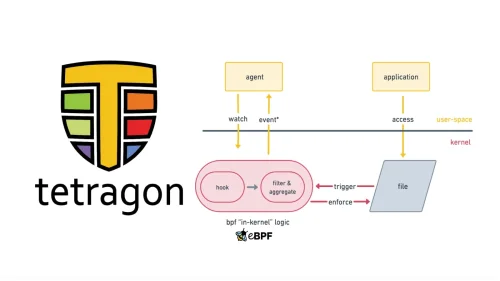
File Monitoring with eBPF and Tetragon (Part 1)
Learn how to implement secure and scalable file monitoring(FIM) with eBPF and Tetragon
Read more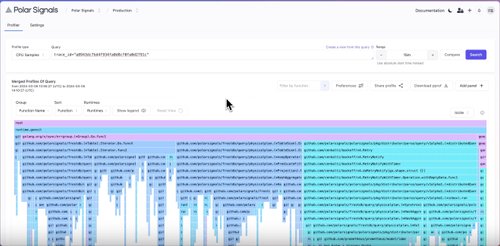
Correlating Tracing with Profiling using eBPF
Learn how to use ebpf-based Parca-Agent to read the trace ID from a target program with Go
Read more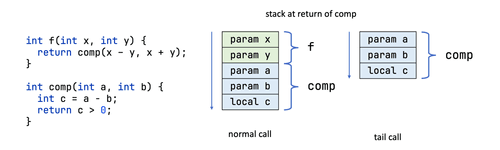
Hello eBPF: Tail calls and your first eBPF application (4)
In the 4th part of the series, you'll finish the chapter 2 of the Learning eBPF book, learn how to use tail calls and the hello-ebpf project as a library and implement one of the book’s exercises
Read more
Adventures in eBPF
An exploration of eBPF highlighting how build a program that leverages eBPF to intercept SSL traffic in user-space
Read more
eBPF program creation in practice – PID concealment (Part 1)
Learn how to create an eBPF program using a tracepoint
Read more
eBPF Up and Running: Part 1
A simple introduction to writing your first eBPF program using C and Golang
Read more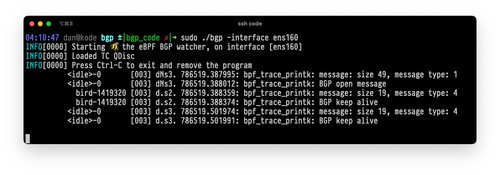
Perfecting Protocol Parsing (Probably) with eBPF
Learn how to parse BGP messages with eBPF
Read more